Building the Encrypted Supercomputer
.png&w=3840&q=75)
Building the Encrypted Supercomputer – DAWN Black Box to Power Arcium’s Encrypted Compute
TLDR:
- Arcium × DAWN Partnership: DAWN nodes will become integrated Arcium Arx Nodes, capable of securely performing computations directly on encrypted data.
- Problem: Today, user data must be decrypted to perform computations, exposing sensitive information and forcing users to trade privacy for convenience, especially as workloads move to decentralized edge devices.
- Arcium’s Unique Value: Arcium combines Multi-Party Computation (MPC) with user-friendly tooling to build a decentralized encrypted supercomputer, enabling secure, scalable computation on encrypted data and making privacy-preserving technologies accessible for any developer.
The people are building a new Internet—one household, and one Black Box at a time. As a decentralized Internet moves from possibility to inevitability, certain core technologies and protocols emerge as essential foundations of this landscape. In this series, we explore these history-defining protocols, highlighting their unique roles in enabling a consumer-owned digital, why each is indispensable, and how the Black Box is designed specifically to bring their benefits directly to households.
The Internet has learned to lock data down almost everywhere, when it’s stored, and when it’s in transit, but there’s one moment we still have to expose data: when it’s actively being used. Data must be decrypted before an application can use it, making it vulnerable to attack and misuse. In the pursuit of building a decentralized, people-powered Internet, workloads will get pushed to the edge, and that means so will the sensitive data.
Think of DNA services like 23andMe. You upload your raw genome hoping to connect with new relatives, or learn about health markers. The moment that file is processed, your entire genetic blueprint exists on someone else’s server. Copies can be analyzed, sold, or subpoenaed (often without your knowledge) because the computations on that genome can’t happen on encrypted data. That’s some of your most sensitive data and you’re going to have to fight toget back control of it. And that’s just one example – think health data from smartwatches, financial information, personal photos, and more. In the advent of AI these things become one hundred times more vulnerable. Until we can compute on data while it remains encrypted, every workflow forces us to trade privacy for convenience.
Fortunately, promising technologies are emerging to solve exactly this problem. Approaches like Fully Homomorphic Encryption (FHE) and Zero-Knowledge Proofs (ZKPs) are at the cutting edge of cryptographic research, and they enable code to operate directly on encrypted data without ever exposing it. This means your genome, medical scans, or personal photos could remain encrypted end-to-end, even as applications use that data to provide you with a service.
But these methods aren’t yet plug-and-play. Depending on the operation developers want to perform—like training AI models tailored for you, or analyzing sensitive medical records—these cryptographic approaches can require a lot of computational resources. On top of the performance hurdles, the developer experience remains daunting (I would know, one of my first crypto projects was building Texas Hold’em without a house). Few standard frameworks exist, and those available often require deep cryptographic expertise to use. As a result, encrypted computation has largely stayed confined to research labs or highly specialized enterprise environments. Even cutting-edge crypto projects aren’t using this technology where they should. To make this technology accessible for a decentralized internet, developers need straightforward tools, user-friendly APIs, and ready access to scalable infrastructure.
Arcium: A Decentralized, Encrypted Supercomputer
Arcium tackles exactly this gap. Rather than forcing developers to become cryptography experts or invest in complicated hardware, Arcium delivers encrypted computation with ease. Their solution is clever but straightforward: developers simply define the function(s) in their program that they want to encrypt and Arcium handles the rest. Arcium leveraged Multi-Party Computation (MPC) as its core cryptographic primitive to enable computation over fully encrypted data. Here's how it works: data is encrypted and computations are defined using MXEs (Multiparty Execution Environments), then securely split up across several independent Arx nodes to be executed. Nodes are organized via clusters, which can be assigned to one or multiple MXEs. Each node executes a portion (or a “secret share”) of the data to compute, so no single node ever sees the full dataset. After the nodes finish their individual pieces, their encrypted results are recombined into a final result. Throughout this process, cryptographic proofs verify that the computations were performed correctly, without anyone ever seeing private data.
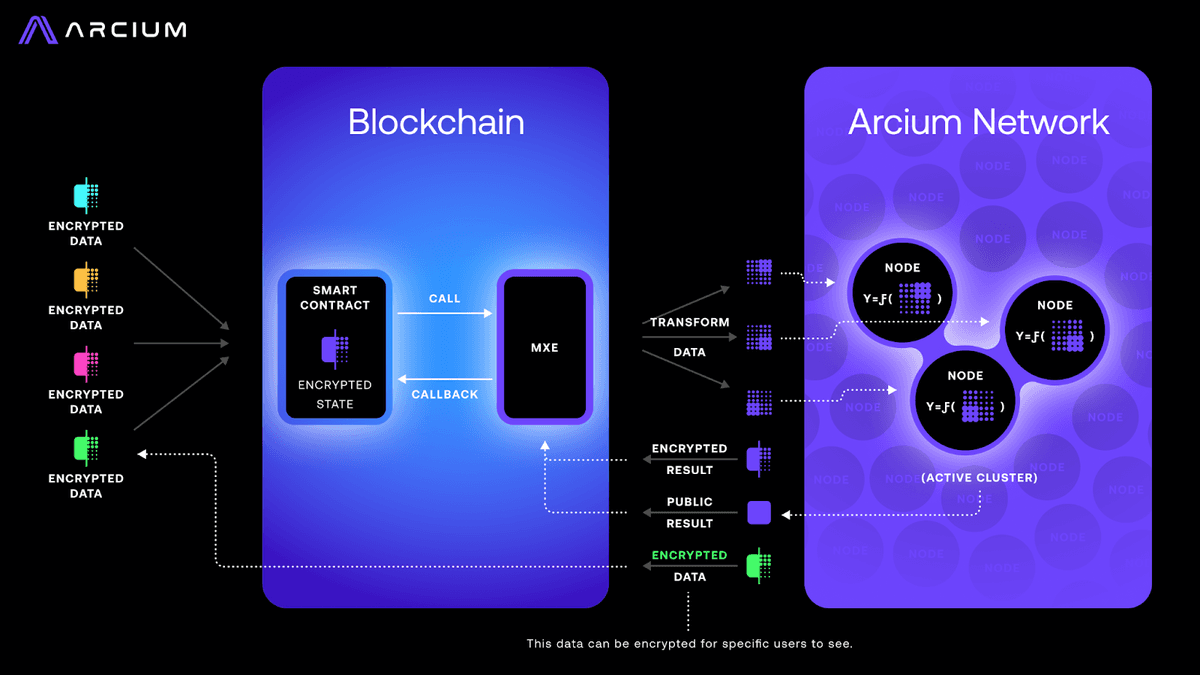
Arcium is built to be accessible for developers. Instead of dealing directly with complicated cryptography, developers use Arcis, Arcium's developer toolkit, to define encrypted functions—much like they do when batching a normal cloud workload.
That’s it. No specialized hardware or crypto PhD required. Arcium transforms what has traditionally been advanced research into a practical tool, making encrypted computation accessible to any developer and laying an essential building block for a decentralized, privacy-focused Internet.
Arcium × DAWN: Building a New Cluster from Consumer Hardware
We’re excited to announce that each DAWN Black Box will operate as a fully integrated Arx Node, which participates in Arcium’s network. The Black Box uniquely bridges the gap between mass-market accessibility and near data-center-grade performance, making it ideal infrastructure for Arcium's confidential computing ecosystem.
With 10-core CPUs and GPUs equipped with up to 20GB of VRAM, each Black Box provides the computational horsepower needed for even the most demanding cryptographic tasks, including advanced methods like Fully Homomorphic Encryption. The result is a cluster of thousands of accessible and powerful nodes capable of securely performing complex encrypted operations, right at the network's edge.
Looking forward, it’s tough to imagine a decentralized Internet without a solution like Arcium. Just as HTTPS transformed expectations for online security—symbolized today by the familiar green lock when you visit a website—MPC could set a new privacy standard. Imagine visiting a website and seeing not just a green lock for HTTPS, but also a purple Arcium lock, certifying that the service’s backend has been independently verified to operate entirely on encrypted data. This simple visual cue could instantly reassure users that their most sensitive information remains secure, no matter what service they’re using. If encrypted computation became the default, the entire internet could be safer and more trustworthy—and that’s exactly the future Arcium and the DAWN Black Box are building towards.